top of page

Blog


Do Not Let WeChat’s Court Victory Give False Security
Used for messaging, social media, and payment transfers, the WeChat application enjoys over one (1) billion user worldwide. Owned by...
Oct 26, 20203 min read


OCR and FTC Issue Seven-Figure Fines for Cyber Law Faux Pas
The Department of Health and Hospitals Office of Civil Rights (“OCR”) and the Federal Trade Commission issued fresh sets of fines for...
Oct 20, 20203 min read


HEALTHCARE ENTITIES MUST INVEST AND THINK LIKE TECHNOLOGY COMPANIES
The Hippocratic oath, which requires physicians to “do no harm” in the name of medicine, should be re-drafted to include prioritizing the...
Oct 14, 20203 min read


Capital One Data Breach Litigation Continues – All Preventable
It’s old news that on July 19, 2019, Capital One Bank learned that a cyber-criminal gained access to 14 years of credit card holder and...
Oct 13, 20203 min read


ECONOMICS OF CYBER CRIME
Two questions on cybercrime yield valuable intel for potential victims: 1) Aside from ransomware, how do cyber criminals make money; and...
Oct 10, 20203 min read


Sanctioning Ransomware Victims Creates Catch-22
Another example of failed communication between private industry and government is the U.S. Department of Treasury, Office of Foreign...
Oct 4, 20203 min read


The Cybersecurity War is Here, and Everyone is a Combatant
Unlike traditional warfare, cyber-crime respects no boundaries or sovereignties and fails to differentiate between combatants and...
Sep 28, 20203 min read


CMMC UNDER INCREASED SCRUTINY FOLLOWING ALLEGATIONS OF CORRUPTION
Good luck to Kate Arrington, the Department of Defense’s CISO, who just inherited a disaster from former members of the Cybersecurity...
Sep 27, 20202 min read


FAILURE TO COMMUNICATE: U.S. Laws Working Against Best Practices
“What we’ve got here is a failure to communicate!” Since birth, my father quoted this to me from the 1967 Paul Newman film Cool Hand Luke...
Sep 16, 20203 min read


WTF is the Difference Between Privacy, Data Protection, and Cybersecurity?
The terms “privacy,” “cybersecurity,” and “data protection” are thrown around, ignorantly and interchangeably despite the noteworthy...
Sep 13, 20202 min read


California Expected to Join Illinois in Regulating Genetic Data
Companies like Ancestry, 23andMe, and MyMedLab need to pay attention. Poised for its Governor’s signature, California’s SB-980 entitled...
Sep 9, 20203 min read

BEWARE THE BOTNETS
More companies are making remote work a permanent status. With the initial push to remote work necessitated by COVID-19 and then...
Aug 31, 20202 min read


A CYBER LAW WIN FOR BANKING!
After years of bad press, banking giant Wells Fargo Bank, N.A. ("Wells Fargo") received a small reprieve in the United States District...
Aug 26, 20204 min read


DO NOT LIE TO THE FTC
On August 20, 2020, 52-year-old former Chief Security Officer (“CSO”) for Uber Technologies Inc. (“Uber”) Joseph Sullivan was charged...
Aug 21, 20203 min read

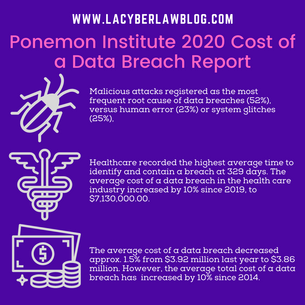
DATA BREACH METRICS FROM 2019 TO 2020: Overall Decrease in Cost, but Increase in Cost for Healthcare
Published by IBM Security, the Ponemon Institute released its 2020 Data Breach Report, which unsurprisingly a marked increase in the...
Aug 14, 20203 min read


4 LESSONS FROM THE IN RE SOLARA MED. SUPPLIES CASE AND DATA BREACH
A United States District Court again allows a lawsuit seeking to hold a commercial data breach victim accountable for its potential role...
Aug 9, 20204 min read


Business Identity Theft: Risks and Prevention
Cyber criminals steal business identities, increasingly targeting recently defunct entities that perished in the pandemic. Business...
Aug 3, 20203 min read


CYBERSECURITY CASE WATCH – BESSEMER v. FISERV
Despite the immature procedural history, Bessemer v. Fiserv is fascinating expose of possible legal liabilities when a MSP/MSSP allegedly...
Aug 1, 20204 min read


The Biggest Lesson from the Twitter Breach
On July 15, 2020, approximately 130 Twitter accounts were “hacked” by bad actors who gained control of the accounts and sent tweets on...
Jul 27, 20203 min read


Schrems II and the Future of Privacy
By Brandon M. Stevens, Attorney, CIPP/US, CIPP/E, CIPM Contributing Writer On July 16, Austrian lawyer and privacy activist Max Schrems...
Jul 23, 20203 min read
bottom of page




